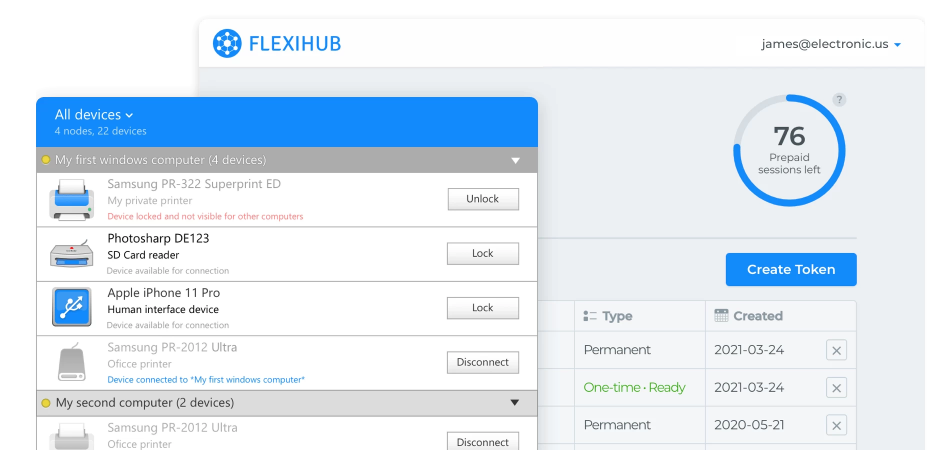
Understanding USB over IP Technology
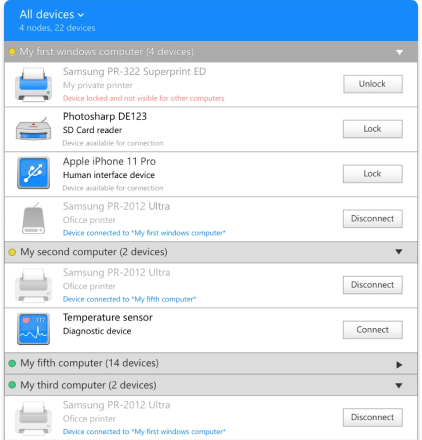
USB over IP software works by employing a combination of virtualization and encapsulation. This enables computers without physical USB ports to access USB devices. Data from a USB device is encapsulated so it can be transferred across a TCP/IP network. The information is then de-encapsulated by a virtual USB port implemented by the USB over TCP/IP software.
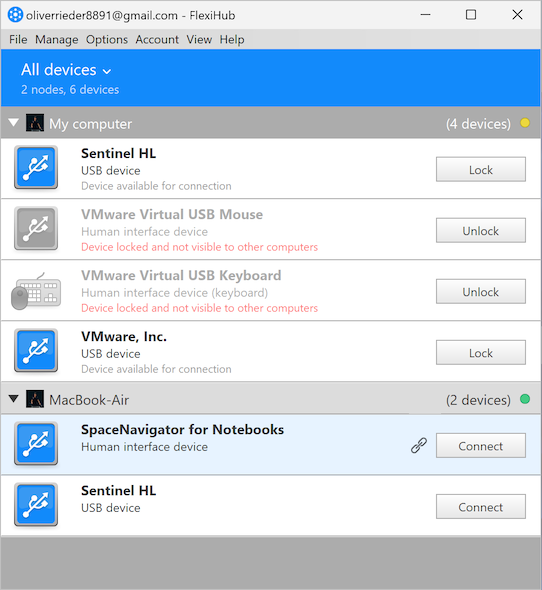
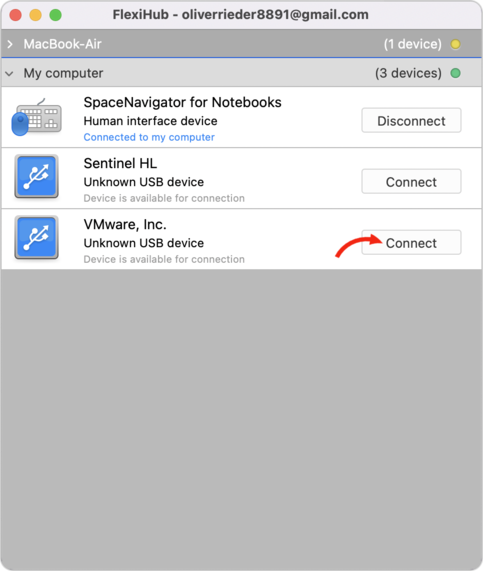
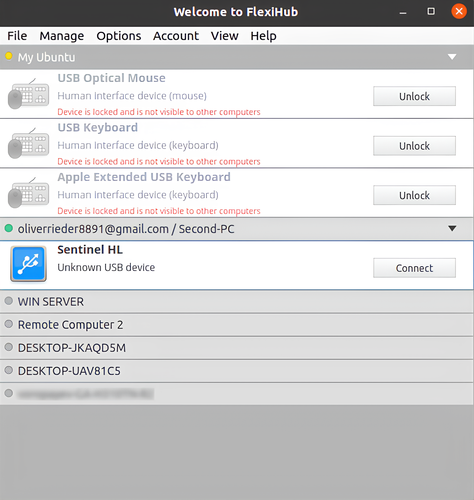
A USB to IP implementation requires the software to be installed on the computer that is physically connected to a USB device that will be shared over the network. The same software is also installed on all remote machines that will access the peripheral over the network.
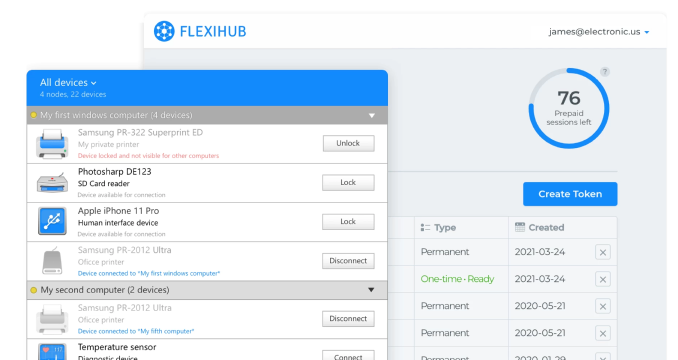
It lets an organization share USB equipment over IP networks without needing to install device drivers on the remote machines. The tool creates secure communication channels through which USB data can be transmitted over the Internet or a private internal network.