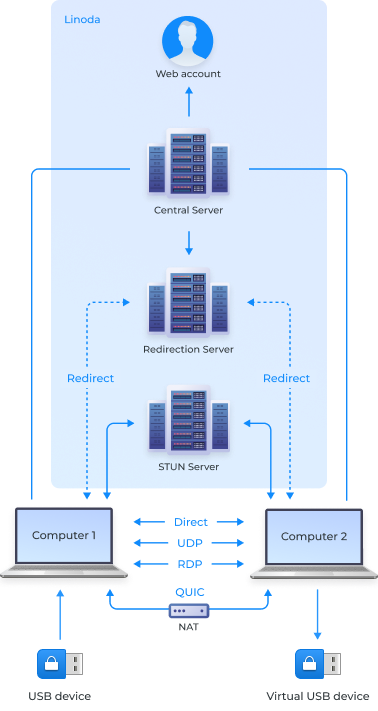
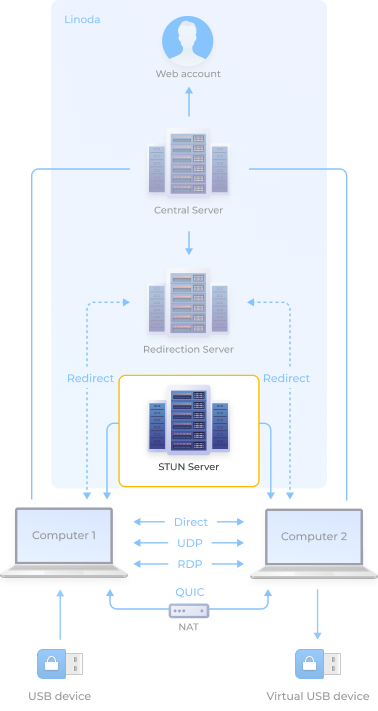
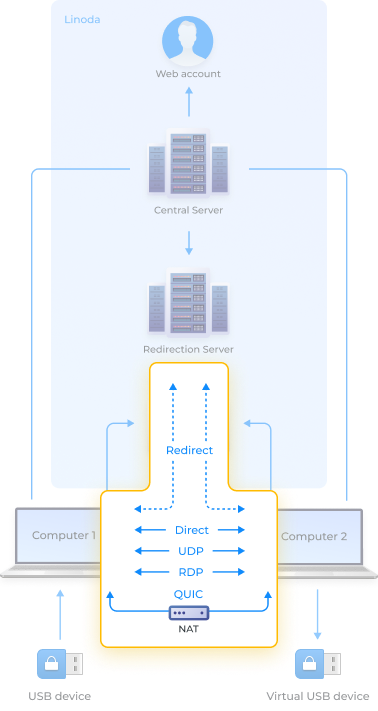
Direct connectionPriority #1
Point-to-point connection, all data is transferred directly from Computer 1 to Computer 2 without intermediaries. The fastest connection option available.
QUICPriority #2
Alleviates some of the issues with NAT by circumventing it. Encapsulation effectively allows the protocol to establish a UDP tunnel through NAT, making it possible to create and maintain a connection.ter.
UDPPriority #3
Point-to-point connection, all data is transferred directly from Computer 1 to Computer 2. Less stability compared to the direct option, but with the added possibility to bypass restrictions when direct communication via TSP is not possible.
RDPPriority #4
Point-to-point connection, all data is transferred directly between Computer 1 and Computer 2 through the Microsoft RDP channel.
RedirectPriority #5
Allows you to connect any pair of nodes with Internet access, but has the lowest bandwidth, since the data is transmitted through a repeater. This is the only connection type to send device data through our server.