FlexiHub Team uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.

Over the last decade, many companies have continued to build security access control systems based on iris recognition technology. Depending on the desired security level, you can use an iris scan to control a central access point within the company's premises or determine access permission across multiple geographic locations.
For example, international air corporations around the world use iris technology to control the flow of crew members and to verify passengers who are authorized to board an aircraft. This biometric system requires fast and secure access to a database that contains the information of all authorized personnel.
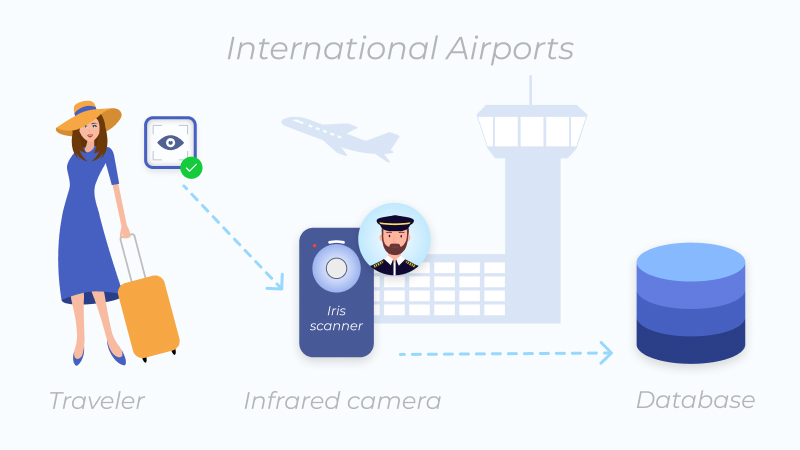
For an iris scanner access control to work, you need a specialized digital camera that uses visible and near-infrared light. Combining these lights allows the camera to take high-contrast pictures of a person's iris.
Once you stand in front of the camera, the scanner detects and excludes reflections that may typically block the iris. The camera lens then focuses on the edge of the iris, the center of the pupil, the eyelids, the eyelashes, and the edge of the pupil.
All unique eye characteristics are converted into digital iris codes that contain 512 digits. These digits are then stored on the computer's database, together with the individual's name and registration details.
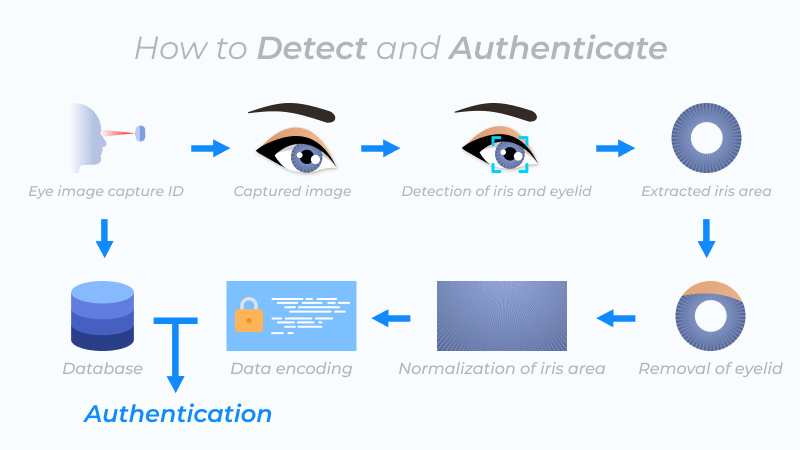
It takes the scanner a few minutes to complete the onboarding process. The device automatically takes a picture of the eye and spends about 0.5 seconds reading the iris pattern. Once the scanner documents the iris pattern, it compares it with previously recorded templates within the database.
Iris recognition control systems continue to have widespread use within the security industry. Despite its broad use case, the technology still has some shortcomings when compared to other biometric control systems.
Biometric control systems are now used as an alternative to older authentication methods like PINs, passcodes, access keys, plastic cards, bank details, and numeric codes. This section explains the various ways iris technology can be used in security systems.
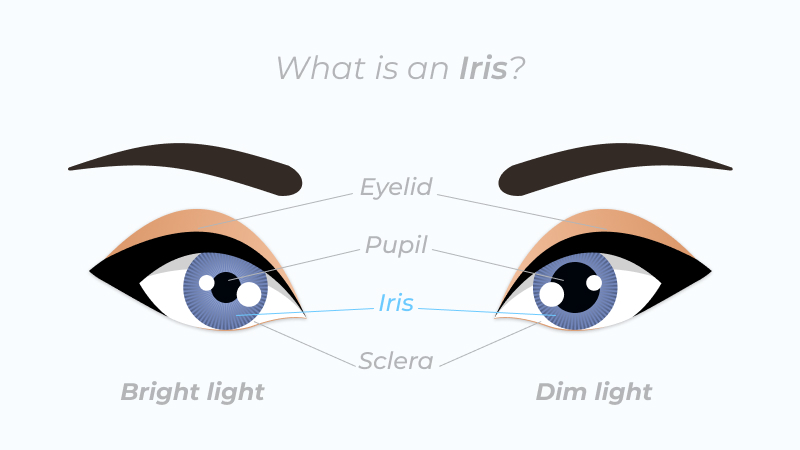
Similar to fingerprint patterns, the iris is a unique characteristic used for biometric identification. Unlike a fingerprint scanner that uses 16 key points to determine user identity, an iris scanner uses about 260 key points that are unique to every eye. The scanner uses these key points during the verification process to develop an encrypted code unique to a single iris.
The scanner stores every iris code on a database and uses that code to create a template. Because the template takes up very little space, you can easily authenticate a user with few computing resources.
For accounting and access control systems that use an iris recognition technology, the chances that an unauthorized person gains access to the system is around 0.00001%; the chances that an authorized personnel is rejected incorrectly is 0.016%
The general consensus is that it is impossible to forge someone's iris identity. This reasoning stems from the fact that the human eye contains unique reflective characteristics which the scanner considers when processing information.
For additional security, some scanners record involuntary eyeball movements unique to a living individual (it is impossible to recognize a dead person because the pupil dilates, making it impossible for the machine to scan). Aside from medical surgery or severe injury, an individual's iris characteristics are unlikely to change.
Just like every other biometric access control system, iris recognition technology is not immune to imperfection. These issues relate to the technology and its deployment. Here's a list of things to consider before you purchase one.
Iris recognition tech remains one of the most promising areas of biometric access control. In the global market, it is estimated that the US, Canada, Japan, Europe, and China will reach an estimated market share of US$4.9 Billion by 2027.
Iris access control remains one of the leading industries in biometric technology. The most pressing area of development is in improving non-invasive recognition by developing high-tech sensors. Because it is relatively easier to implement cloud biometrics than on-premises biometric solutions, many companies are in the race to migrate and integrate their biometric identification system to the cloud.
In order to implement efficient cloud scenarios, you need a system that allows you quickly and securely connect a remote biometric scanner to your cloud server. FlexiHub can easily handle this. Feel free to contact our representatives to get started today!
